A Comprehensive Guide to Memory Mapping: Understanding mmap() and its Applications
Related Articles: A Comprehensive Guide to Memory Mapping: Understanding mmap() and its Applications
Introduction
With great pleasure, we will explore the intriguing topic related to A Comprehensive Guide to Memory Mapping: Understanding mmap() and its Applications. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
A Comprehensive Guide to Memory Mapping: Understanding mmap() and its Applications
Introduction
Memory mapping, a powerful technique employed in modern operating systems, provides a mechanism for directly accessing files and other resources within a program’s address space. This method, implemented through the mmap() system call, offers significant advantages in terms of performance, efficiency, and memory management. This article delves into the intricacies of memory mapping, exploring its underlying principles, implementation details, and diverse applications.
Understanding Memory Mapping
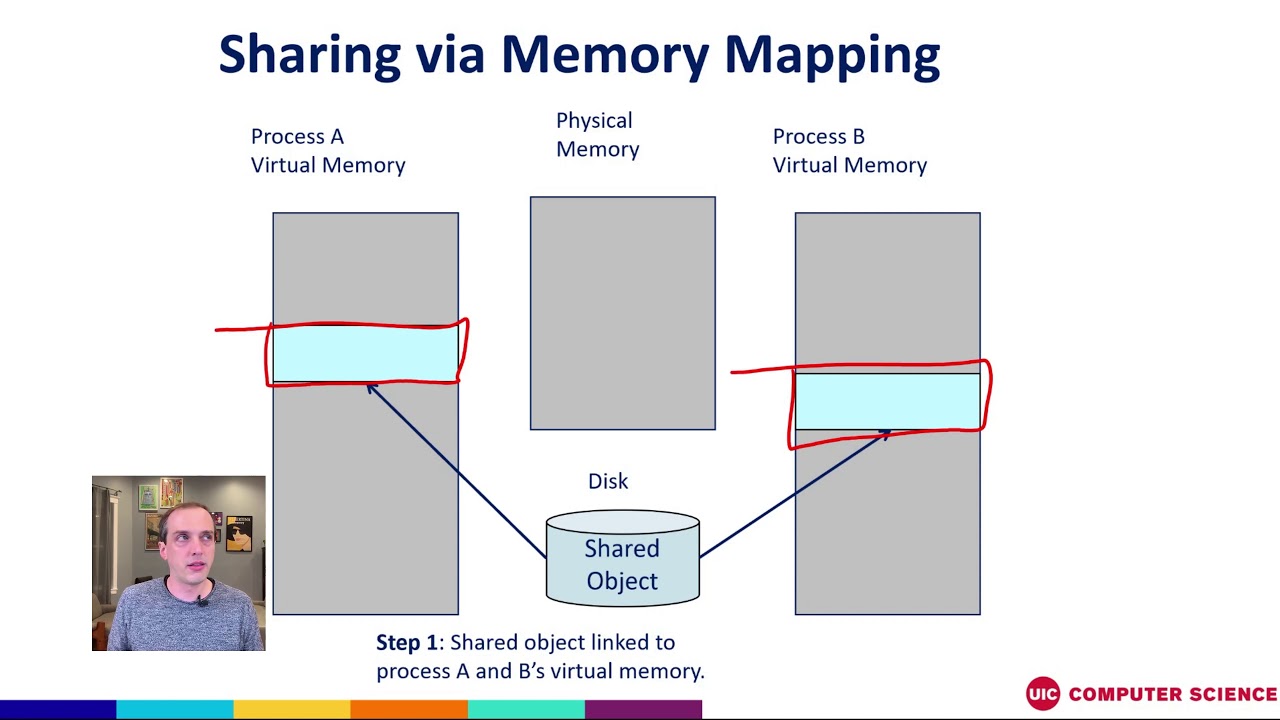
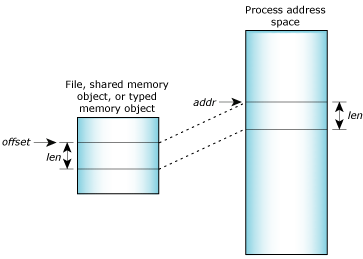
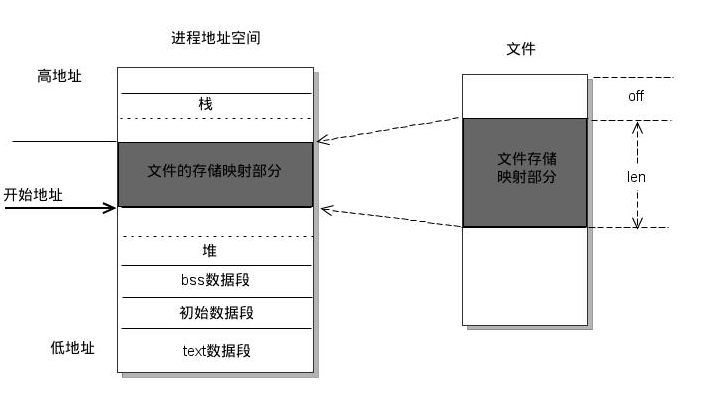
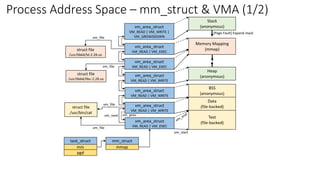
At its core, memory mapping establishes a direct connection between a file or other resource residing in the operating system’s file system and a region of the program’s virtual memory. This connection allows the program to treat the mapped resource as if it were directly located in its own memory space, enabling efficient access and manipulation.
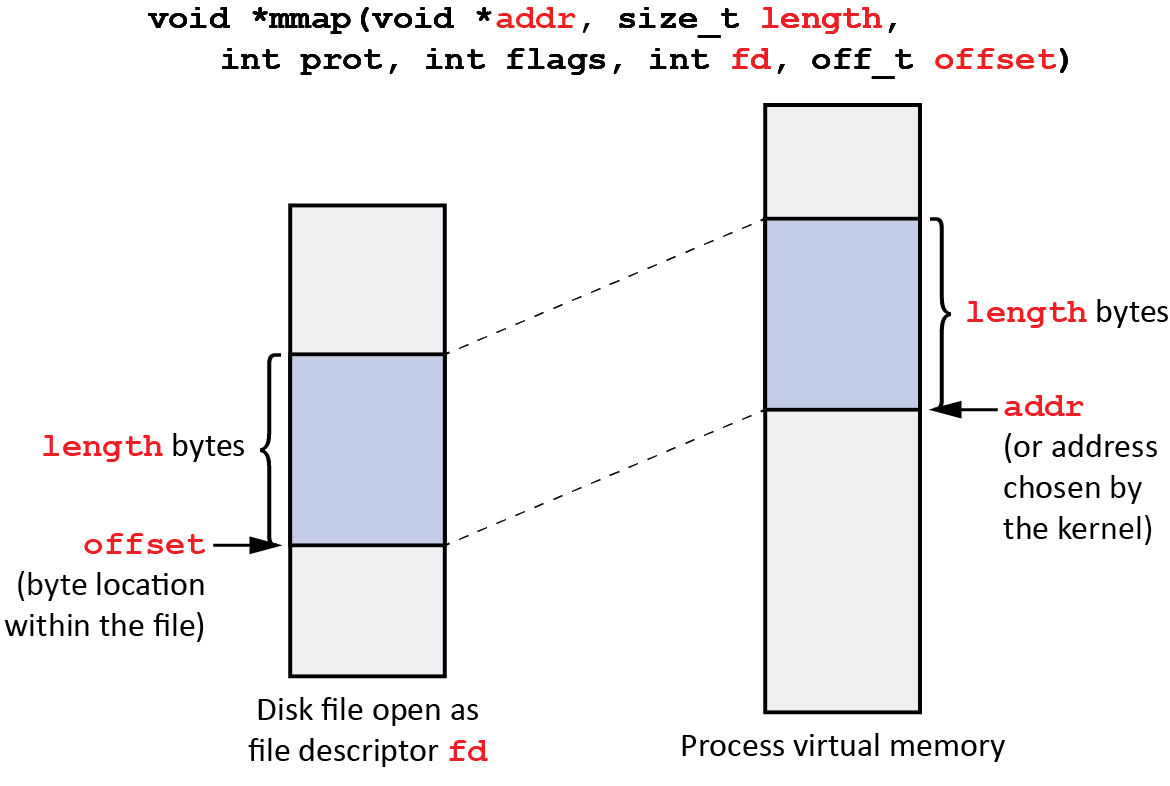
The mmap() System Call
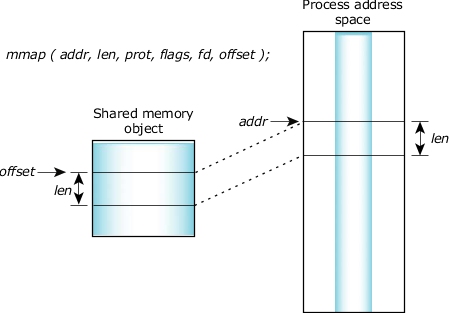
The mmap() system call serves as the primary interface for memory mapping. It allows a process to create a mapping between a file or device and a region of its virtual address space. The call typically takes the following arguments:
- Address: A suggested starting address for the mapping, which the system may adjust.
- Length: The size of the memory region to be mapped.
- Protection: Flags specifying the desired access permissions (read, write, execute).
- Flags: Options that modify the behavior of the mapping, such as shared or private mappings.
- File Descriptor: A file descriptor representing the file or device to be mapped.
- Offset: The offset within the file from which mapping should begin.
Upon successful execution, mmap() returns a pointer to the mapped memory region. This pointer can then be used by the program to access and manipulate the data contained within the file.
Types of Mappings
Memory mappings can be categorized into two primary types:
- Shared Mappings: These mappings allow multiple processes to share the same memory region, providing a mechanism for inter-process communication and data sharing. Modifications made by one process are immediately reflected in the shared memory region, visible to all other processes sharing the mapping.
- Private Mappings: These mappings are exclusive to a single process, offering a private copy of the mapped data. Changes made to the mapped region are not visible to other processes.
Advantages of Memory Mapping
Memory mapping offers several advantages over traditional file I/O methods:
- Performance Enhancements: Direct access to data within the program’s address space eliminates the overhead associated with system calls for file read/write operations, resulting in significant performance gains, especially for large files or frequent access patterns.
- Memory Management Efficiency: Memory mapping allows the operating system to manage memory allocation more effectively, dynamically allocating and releasing memory as needed. This approach reduces fragmentation and improves overall memory utilization.
- Simplified Data Access: Memory mapping simplifies data access by providing a unified view of data, regardless of its physical location. Programs can treat both in-memory data and data stored in files as if they were located in the same memory space.
- Shared Memory Communication: Shared mappings provide a robust mechanism for inter-process communication, enabling efficient data exchange between multiple processes.
Applications of Memory Mapping
Memory mapping finds widespread use in various programming domains, including:
- Database Systems: Memory mapping is frequently employed in database management systems to efficiently manage large data files, enabling fast data access and manipulation.
- Web Servers: Web servers leverage memory mapping to efficiently serve static content, caching files in memory for faster delivery to clients.
- Multimedia Applications: Memory mapping plays a crucial role in multimedia applications, facilitating efficient access and processing of large audio and video files.
- Scientific Computing: Scientific simulations and data analysis often involve processing massive datasets, making memory mapping an essential tool for efficient data handling.
- Game Development: Games frequently utilize memory mapping to manage game assets, such as textures, models, and levels, improving loading times and performance.
Considerations and Best Practices
While memory mapping offers significant advantages, it’s important to consider several factors and best practices for its effective utilization:
- Memory Consumption: Memory mapping can consume significant amounts of memory, especially when dealing with large files. It’s essential to carefully consider the memory footprint of mappings and ensure sufficient available memory to avoid system instability.
- Data Consistency: In shared mappings, ensuring data consistency across multiple processes is crucial. Synchronization mechanisms, such as mutexes or semaphores, should be employed to prevent race conditions and maintain data integrity.
- Mapping Management: Proper management of memory mappings is essential. Programs should unmap regions when they are no longer needed to free up memory resources.
-
Error Handling: It’s crucial to handle errors during the
mmap()call and other memory mapping operations. Proper error handling ensures program stability and prevents potential crashes.
Frequently Asked Questions (FAQs)
1. What is the difference between mmap() and malloc()?
mmap() allocates memory from the file system, mapping a file or device into the process’s address space. malloc() allocates memory from the heap, a region of memory managed by the program.
2. Can I map multiple files into the same memory region?
No, you cannot directly map multiple files into the same memory region. However, you can use techniques like offsetting within a single file or employing shared memory mechanisms to achieve similar functionality.
3. What happens if I modify a mapped file?
Modifications made to a mapped file are reflected in the original file, depending on the mapping type. Private mappings allow modifications to the mapped region without affecting the original file, while shared mappings propagate changes to all processes sharing the mapping.
4. Is memory mapping suitable for all applications?
Memory mapping is not suitable for all applications. It’s most effective for applications that require frequent access to large files, benefit from shared memory communication, or have performance-critical data access patterns.
5. What are the security implications of memory mapping?
Shared mappings can introduce security vulnerabilities if not properly managed. Unintentional access or modification of shared memory regions by unauthorized processes can lead to security breaches.
Tips for Effective Memory Mapping
- Use shared mappings cautiously: Shared mappings offer advantages but can introduce complexities in managing data consistency and synchronization. Use them only when necessary.
- Unmap regions when no longer needed: Release memory resources promptly by unmapping regions that are no longer required.
-
Handle errors carefully: Implement robust error handling for
mmap()and other memory mapping operations to ensure program stability. - Consider memory usage: Be mindful of the memory consumption of mappings, especially when dealing with large files.
- Optimize for performance: Explore techniques like page locking to minimize page faults and optimize data access performance.
Conclusion
Memory mapping, through the mmap() system call, offers a powerful and efficient mechanism for accessing files and other resources within a program’s address space. It provides significant performance enhancements, simplified data access, and robust inter-process communication capabilities. By understanding the underlying principles, implementation details, and best practices of memory mapping, developers can leverage its benefits to create efficient and performant applications across various domains.

![MMAP Memory Mapping - [PPT Powerpoint]](https://static.fdocuments.in/doc/1200x630/5695d4fe1a28ab9b02a397ea/mmap-memory-mapping.jpg?t=1686606685)

Closure
Thus, we hope this article has provided valuable insights into A Comprehensive Guide to Memory Mapping: Understanding mmap() and its Applications. We hope you find this article informative and beneficial. See you in our next article!