Memory Mapping in C: A Comprehensive Guide
Related Articles: Memory Mapping in C: A Comprehensive Guide
Introduction
With great pleasure, we will explore the intriguing topic related to Memory Mapping in C: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Memory Mapping in C: A Comprehensive Guide
- 2 Introduction
- 3 Memory Mapping in C: A Comprehensive Guide
- 3.1 Understanding the Fundamentals of Memory Mapping
- 3.2 Unveiling the Mechanics of mmap()
- 3.3 Unlocking the Potential: Advantages of Memory Mapping
- 3.4 Illuminating Real-World Applications
- 3.5 Navigating Common Challenges: FAQs
- 3.6 Unleashing the Power of Memory Mapping: Tips for Effective Implementation
- 3.7 Conclusion: Embracing the Efficiency of Memory Mapping
- 4 Closure
Memory Mapping in C: A Comprehensive Guide
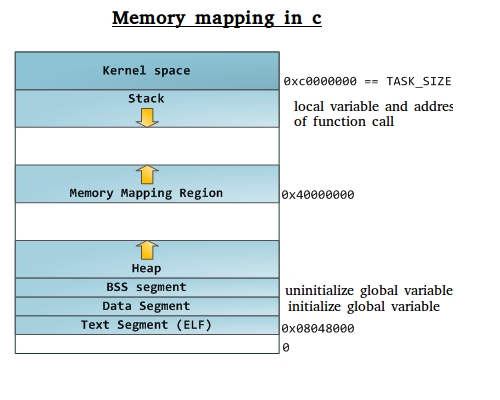
Memory mapping, a powerful technique within the realm of C programming, allows for efficient data access by establishing a direct correspondence between a portion of a file and a region of the process’s virtual address space. This process, facilitated by the mmap() system call, offers a unique approach to file handling, eliminating the need for traditional read and write operations and streamlining data manipulation.
This article delves into the intricacies of memory mapping in C, exploring its core functionalities, advantages, and applications. We will examine its underlying mechanisms, explore common usage scenarios, and address frequently asked questions, providing a comprehensive understanding of this powerful tool.
Understanding the Fundamentals of Memory Mapping
At its core, memory mapping allows a program to treat a file as if it were a contiguous block of memory. This seamless integration eliminates the need for explicit file I/O operations, significantly enhancing performance and simplifying data access.
The process begins with a call to the mmap() function, specifying the file, the desired mapping size, and the desired access permissions. The system then allocates a virtual memory region for the file, making it directly accessible to the program. Any changes made to this mapped region are automatically reflected in the underlying file, eliminating the need for explicit write operations.
Unveiling the Mechanics of mmap()
The mmap() function, a cornerstone of memory mapping, takes several parameters to define the mapping behavior:
void *mmap(void *addr, size_t length, int prot, int flags, int fd, off_t offset);
Parameters:
-
addr: A suggested starting address for the mapping. Setting this toNULLallows the system to choose the most appropriate address. -
length: The size of the memory region to be mapped, expressed in bytes. -
prot: Specifies the desired access permissions for the mapped region. Common options include:-
PROT_READ: Read-only access. -
PROT_WRITE: Read and write access. -
PROT_EXEC: Execute permissions. -
PROT_NONE: No access allowed.
-
-
flags: Determines the behavior of the mapping. Key options include:-
MAP_SHARED: Changes made to the mapped region are visible to other processes that share the same mapping. -
MAP_PRIVATE: Changes made to the mapped region are private to the process and are not reflected in the underlying file. -
MAP_ANONYMOUS: Creates a mapping without an underlying file, allowing for the creation of shared memory segments.
-
-
fd: The file descriptor of the file to be mapped. A value of-1is used for anonymous mappings. -
offset: The offset within the file from which the mapping should begin.
Upon successful execution, mmap() returns a pointer to the starting address of the mapped region. This pointer can be used to access the file data as if it were regular memory.
Unlocking the Potential: Advantages of Memory Mapping
Memory mapping offers a compelling set of advantages over traditional file I/O methods:
- Enhanced Performance: By eliminating the need for explicit read and write operations, memory mapping significantly reduces the overhead associated with file access, leading to faster data processing.
- Simplified Data Access: Memory mapping provides a unified view of file data, allowing for direct access and manipulation as if it were in memory. This simplifies data handling, eliminating the need for complex file I/O routines.
- Efficient Memory Management: Memory mapping leverages the operating system’s virtual memory management capabilities, allowing for efficient use of system resources.
-
Shared Memory Support: The
MAP_SHAREDflag enables the creation of shared memory segments, facilitating communication and data sharing between multiple processes.
Illuminating Real-World Applications
Memory mapping finds its place in a diverse range of applications, showcasing its versatility and efficiency:
- Large File Processing: Memory mapping proves invaluable for handling large files, allowing for efficient access and manipulation of data without loading the entire file into memory.
- Database Systems: Database systems often utilize memory mapping to manage large data files, enabling fast access and concurrent data modifications.
- Image Processing: Image processing applications can leverage memory mapping to efficiently load and manipulate large image files, enhancing performance and reducing memory overhead.
- Network Communication: Memory mapping can be used to create shared memory segments for inter-process communication, streamlining data exchange between network applications.
Navigating Common Challenges: FAQs
Q: What happens when the mapped file is modified outside the process?
A: When the MAP_SHARED flag is used, changes made to the file outside the process are reflected in the mapped region. For MAP_PRIVATE mappings, changes made outside the process are not visible.
Q: How can I ensure data consistency when using memory mapping?
A: To maintain data consistency, it’s essential to use appropriate synchronization mechanisms, such as mutexes or semaphores, especially when multiple processes are accessing the shared mapping.
Q: What are the implications of using MAP_ANONYMOUS for memory mapping?
A: MAP_ANONYMOUS allows for the creation of anonymous mappings, which do not correspond to any underlying file. This is particularly useful for creating shared memory segments for inter-process communication.
Q: What happens when the process terminates while a file is mapped?
A: Upon process termination, the mapped region is automatically unmapped, releasing the allocated memory. Any changes made to the mapped region are written back to the file if the MAP_SHARED flag was used.
Unleashing the Power of Memory Mapping: Tips for Effective Implementation
-
Choose the Right Mapping Flags: Carefully select the appropriate flags based on the specific requirements of your application. For instance,
MAP_SHAREDis ideal for shared memory, whileMAP_PRIVATEis suitable for private data manipulation. - Ensure Data Consistency: Utilize synchronization mechanisms to maintain data consistency, especially when multiple processes are accessing the shared mapping.
- Manage Memory Resources: Properly unmap the memory region when it’s no longer needed to avoid memory leaks and ensure efficient resource utilization.
- Consider File Size: Memory mapping is particularly beneficial for large files. However, for smaller files, traditional file I/O operations might be more efficient.
- Optimize for Performance: Explore techniques such as pre-fetching and caching to further optimize data access and improve application performance.
Conclusion: Embracing the Efficiency of Memory Mapping
Memory mapping in C offers a powerful and efficient approach to file handling, enabling direct access and manipulation of file data within the process’s virtual address space. By eliminating the need for explicit file I/O operations and streamlining data access, memory mapping significantly enhances application performance and simplifies data handling. Its versatility and efficiency make it a valuable tool for a wide range of applications, from large file processing and database systems to image processing and network communication. By understanding the fundamentals of memory mapping, its advantages, and its practical applications, developers can leverage this powerful technique to optimize their C programs for enhanced performance and efficiency.


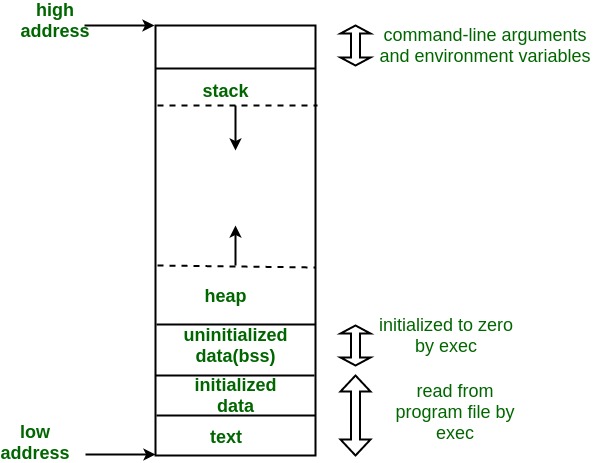
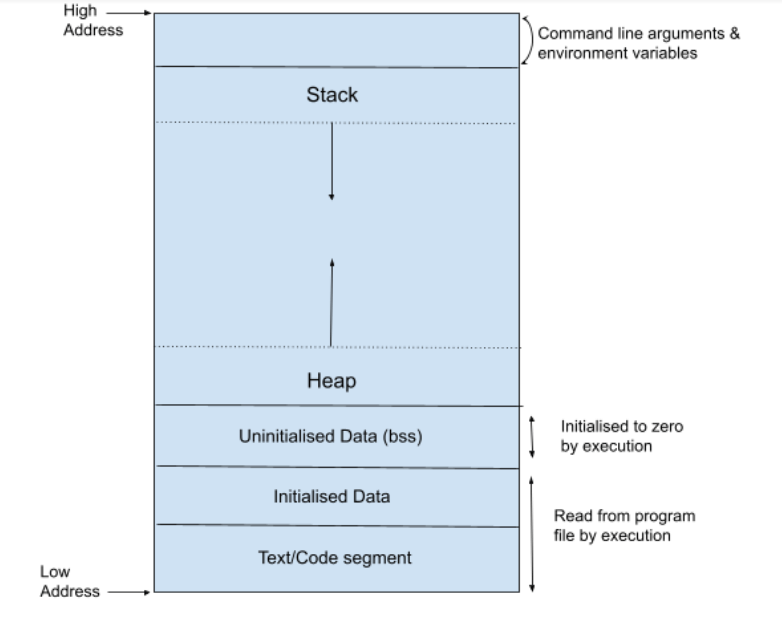
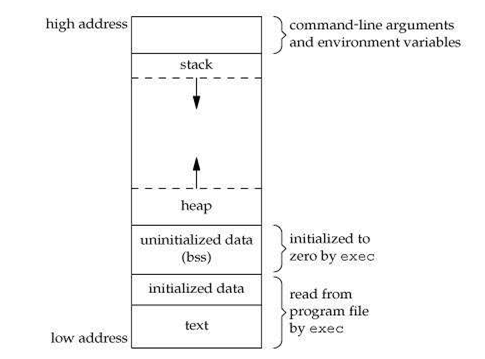
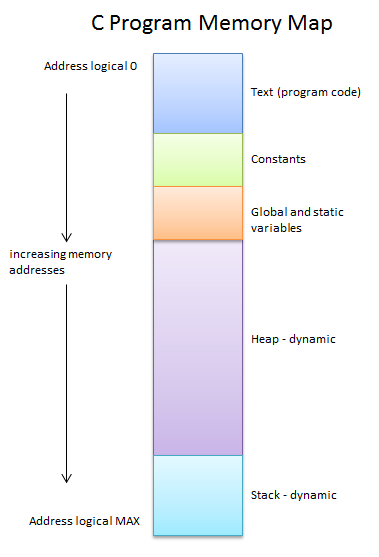
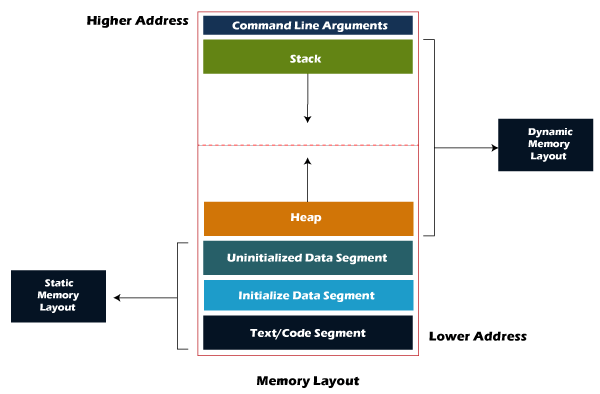

Closure
Thus, we hope this article has provided valuable insights into Memory Mapping in C: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!