Memory Mapping in Linux: A Comprehensive Exploration
Related Articles: Memory Mapping in Linux: A Comprehensive Exploration
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Memory Mapping in Linux: A Comprehensive Exploration. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Memory Mapping in Linux: A Comprehensive Exploration
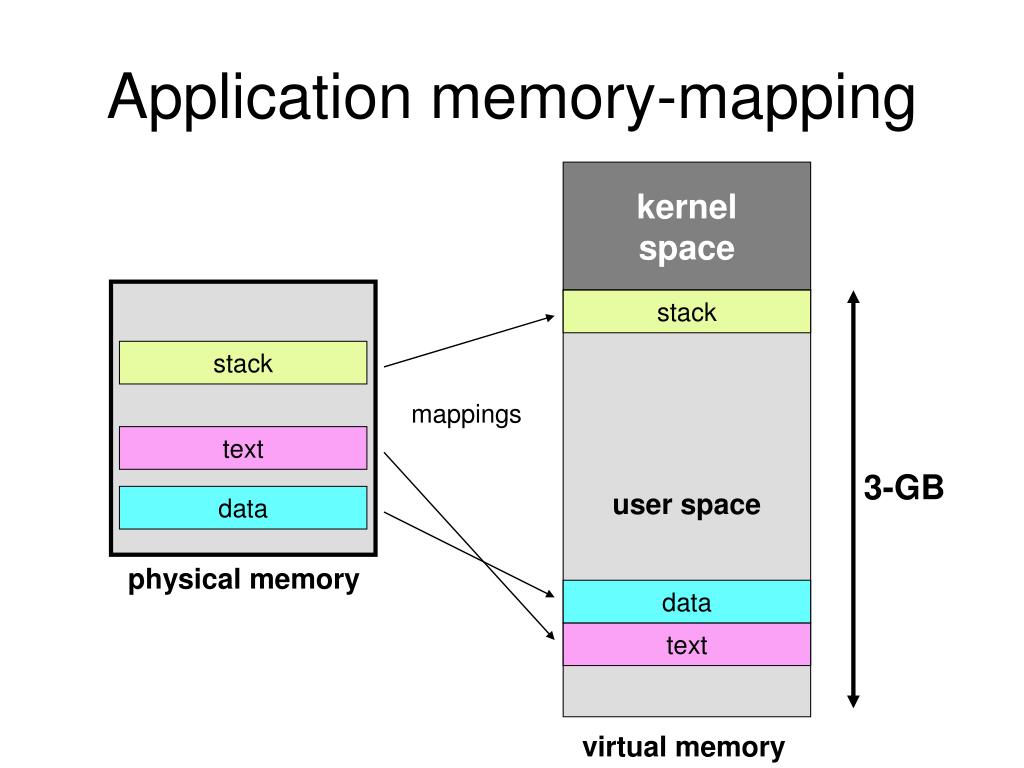
Memory mapping, a powerful mechanism in Linux, provides a unique way to interact with files and memory. It allows processes to access data directly from files without the need for traditional read and write operations, significantly enhancing performance and efficiency. This article delves into the intricacies of memory mapping in Linux, exploring its functionalities, benefits, and applications, while addressing common inquiries and providing practical tips for its effective utilization.
Understanding Memory Mapping
At its core, memory mapping establishes a direct connection between a portion of a file and a region in the process’s virtual address space. This means that accessing the file data is as simple as accessing a memory location. The operating system handles the complexities of managing the underlying file system and physical memory, making it transparent to the application.
The Mechanics of Memory Mapping
The mmap() system call is the cornerstone of memory mapping in Linux. It takes several arguments, including the file descriptor, the desired memory size, the access permissions (read, write, or execute), and flags specifying the mapping behavior. Upon successful execution, mmap() returns a pointer to the mapped memory region.
Benefits of Memory Mapping
Memory mapping offers a compelling set of advantages, making it a preferred approach for various scenarios:
-
Performance Enhancement: Eliminating the need for traditional read and write operations, memory mapping significantly reduces the overhead associated with file I/O. This results in faster data access and improved program performance, especially when dealing with large files.
-
Simplified Data Management: Memory mapping simplifies data handling by treating file contents as part of the process’s address space. This eliminates the need for explicit buffering and file management operations, streamlining the code and reducing the potential for errors.
-
Shared Memory: Memory mapping facilitates inter-process communication by enabling multiple processes to share a common memory region. This shared region can be used for data exchange, synchronization, and other collaborative tasks, providing a powerful mechanism for inter-process communication.
-
Efficient Data Access: Memory mapping allows for efficient access to data within a file, enabling random access and efficient manipulation of specific data segments. This is particularly beneficial for applications that require frequent random access to large files.
Applications of Memory Mapping
The versatility of memory mapping makes it suitable for a wide range of applications:
-
Database Systems: Memory mapping is frequently used in database systems to load large data files into memory for faster access and processing.
-
Image Processing: Image processing applications often employ memory mapping to efficiently access and manipulate large image files.
-
Web Servers: Web servers utilize memory mapping to load static content into memory for faster delivery to clients.
-
Game Development: Game developers leverage memory mapping to improve performance by loading game assets directly into memory.
-
Scientific Computing: Scientific simulations often involve handling massive datasets, where memory mapping is crucial for efficient data management and analysis.
Addressing Common Concerns
1. Memory Consumption: While memory mapping provides performance benefits, it’s crucial to consider the potential memory consumption. If the mapped file is large, it can consume a significant portion of the process’s address space. To mitigate this, it’s essential to carefully choose the appropriate mapping size and use techniques like memory-mapped files with shared memory to manage memory consumption effectively.
2. Data Consistency: Maintaining data consistency when multiple processes share a memory-mapped region can be challenging. Proper synchronization mechanisms, such as mutexes or semaphores, are necessary to ensure data integrity and prevent race conditions.
3. Security Considerations: Memory mapping can expose sensitive data stored in files to unauthorized access. It’s crucial to implement appropriate security measures, such as access control lists and file permissions, to protect sensitive data from unauthorized access.
FAQs about Memory Mapping in Linux
Q: What is the difference between memory mapping and traditional file I/O?
A: Traditional file I/O involves reading data from a file into a buffer in memory and writing data from memory to a file. This process involves multiple system calls and buffer management, which can be time-consuming, especially for large files. Memory mapping eliminates the need for explicit read and write operations by creating a direct link between the file and the process’s address space, allowing for faster and more efficient data access.
Q: How can I create a memory-mapped file in Linux?
A: The mmap() system call is used to create a memory-mapped file. The call requires several arguments, including the file descriptor, the desired memory size, the access permissions, and flags specifying the mapping behavior. The following example demonstrates creating a memory-mapped file for reading and writing:
#include <sys/mman.h>
#include <fcntl.h>
#include <unistd.h>
int main() PROT_WRITE, MAP_SHARED, fd, 0);
if (ptr == MAP_FAILED)
perror("mmap");
return 1;
// Access the memory-mapped region like a normal memory location
// ...
munmap(ptr, 4096);
close(fd);
return 0;
Q: How do I unmap a memory-mapped region?
A: The munmap() system call is used to unmap a memory-mapped region. It takes the address of the mapped region and its size as arguments. The following code snippet demonstrates unmapping a memory-mapped region:
munmap(ptr, 4096);Q: What are the different flags used with mmap()?
A: The mmap() system call accepts several flags to control the mapping behavior. Some common flags include:
-
MAP_SHARED: Creates a shared mapping, where changes made by one process are visible to other processes sharing the same mapping. -
MAP_PRIVATE: Creates a private mapping, where changes made by one process are not visible to other processes. -
MAP_ANONYMOUS: Creates an anonymous mapping, which is not associated with a file. This is often used for shared memory between processes. -
MAP_FIXED: Attempts to map the file at a specific address. This can be useful for performance optimization but can also lead to conflicts if the address is already in use.
Tips for Effective Memory Mapping
-
Choose the Appropriate Mapping Size: Carefully select the size of the memory region to be mapped, ensuring it’s large enough to accommodate the data but not excessively large to avoid unnecessary memory consumption.
-
Use Synchronization Mechanisms: When using shared memory mapping, employ appropriate synchronization mechanisms like mutexes or semaphores to prevent race conditions and ensure data consistency.
-
Consider Performance Trade-offs: While memory mapping can significantly improve performance, it’s essential to consider the potential performance trade-offs. For small files or infrequent access, traditional file I/O might be more efficient.
-
Handle Errors Gracefully: Implement proper error handling mechanisms to gracefully handle potential errors during memory mapping operations, such as
mmap()failures ormunmap()errors.
Conclusion
Memory mapping is a powerful technique in Linux that offers significant performance benefits and simplifies data management. It enables processes to access file data directly from memory, eliminating the need for traditional read and write operations. By understanding the mechanics, benefits, and applications of memory mapping, developers can leverage its capabilities to optimize performance and efficiency in various scenarios, ranging from database systems to scientific computing. However, it’s crucial to carefully consider memory consumption, data consistency, and security implications to ensure its effective and secure utilization.
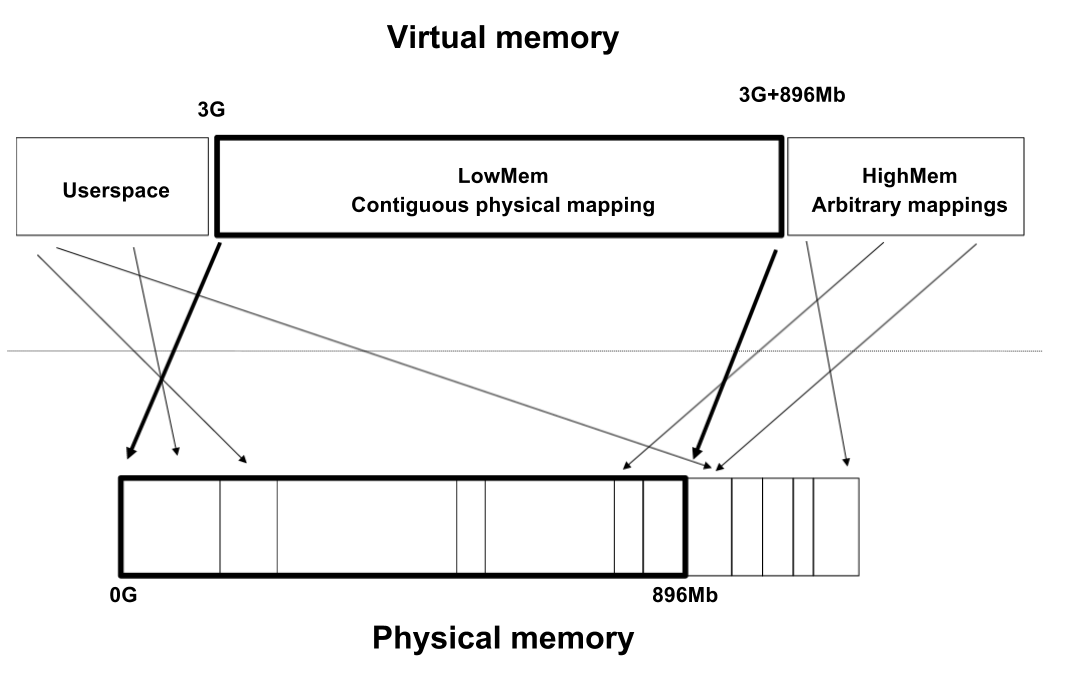

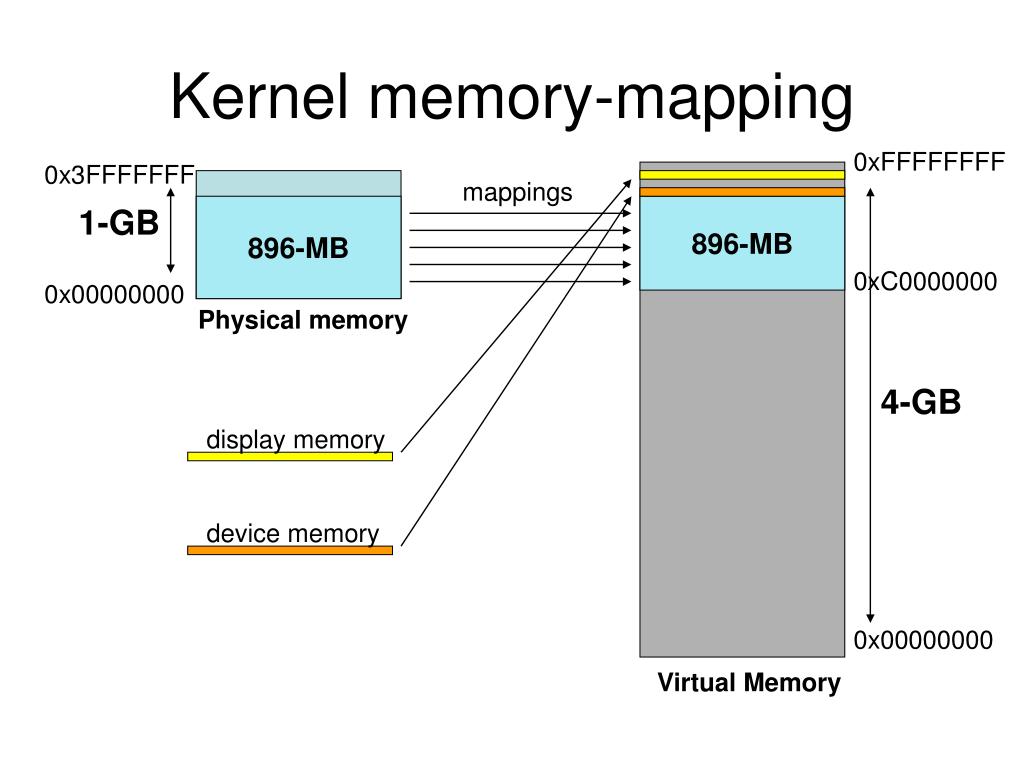
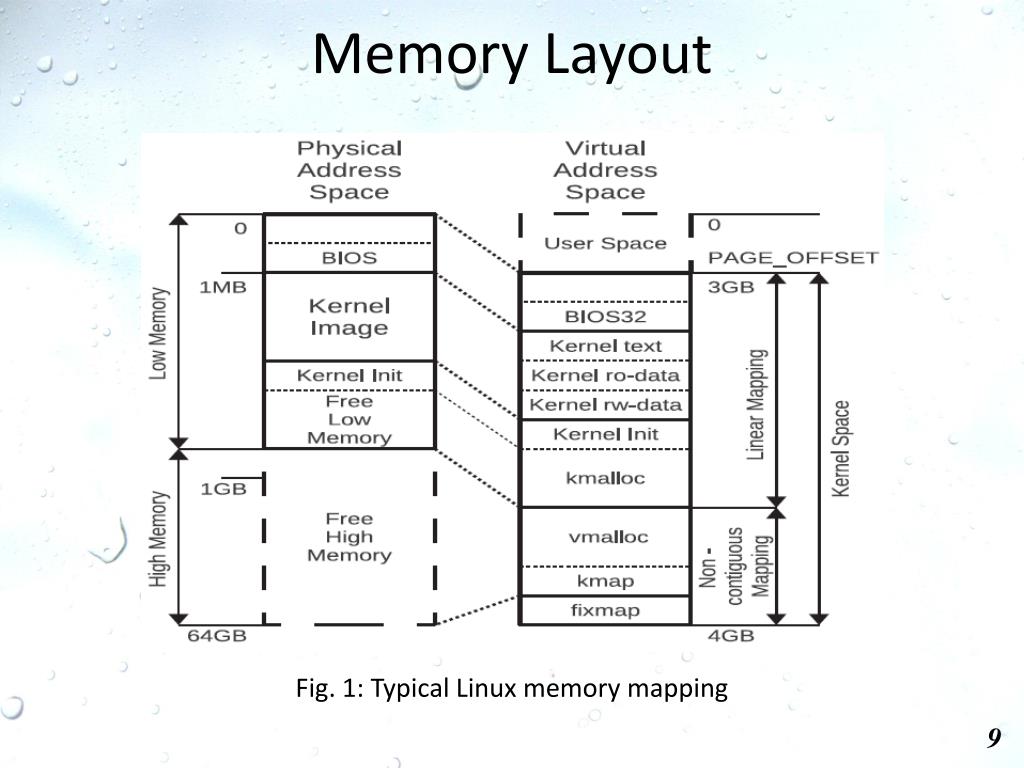



Closure
Thus, we hope this article has provided valuable insights into Memory Mapping in Linux: A Comprehensive Exploration. We appreciate your attention to our article. See you in our next article!