Unveiling the Power of Nmap for Oracle Database Security Audits
Related Articles: Unveiling the Power of Nmap for Oracle Database Security Audits
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling the Power of Nmap for Oracle Database Security Audits. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Power of Nmap for Oracle Database Security Audits

In the realm of cybersecurity, comprehensive network scanning plays a crucial role in identifying vulnerabilities and potential threats. Network Mapper (Nmap), a widely-used open-source tool, provides a versatile framework for network exploration and security auditing. Within this framework, Nmap’s ability to interact with Oracle databases through custom scripts offers a powerful mechanism for assessing database security posture and uncovering potential vulnerabilities. This article delves into the intricacies of Nmap Oracle scripts, exploring their functionalities, benefits, and practical applications.
Nmap Oracle Scripts: A Deep Dive
Nmap’s scripting engine empowers users to extend its capabilities beyond basic port scanning and service detection. Oracle scripts, specifically designed for interacting with Oracle databases, leverage the power of Nmap to perform various security-related tasks, including:
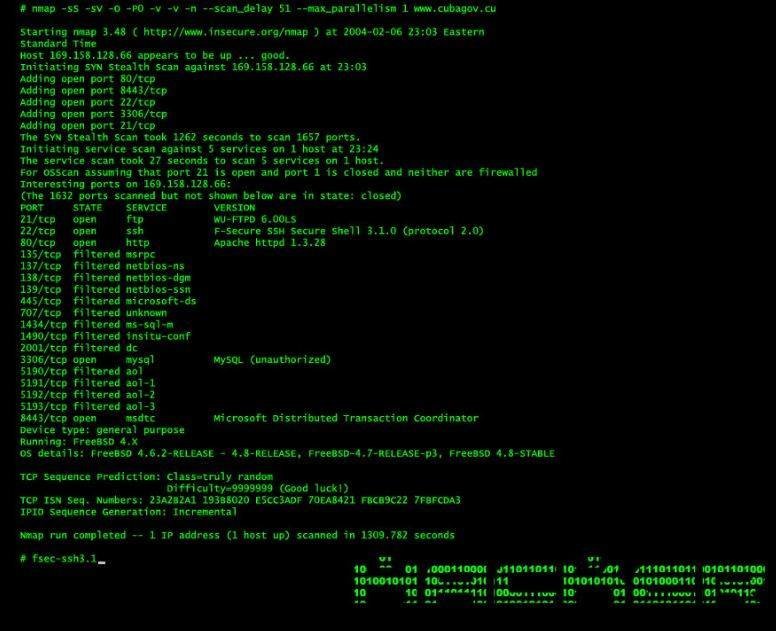
- Version Identification: Oracle scripts can accurately identify the version of the Oracle database running on a target system. This information is vital for understanding the database’s specific vulnerabilities and potential attack vectors.
- Service Detection: Nmap scripts can detect specific Oracle services running on the target system, such as the listener, SQL*Plus, and various database management tools. This knowledge helps in identifying potential points of entry for attackers.
- Vulnerability Scanning: Oracle scripts can be used to scan for known vulnerabilities in the database software itself or in its configuration. This includes checking for common misconfigurations, outdated patches, and known exploits.
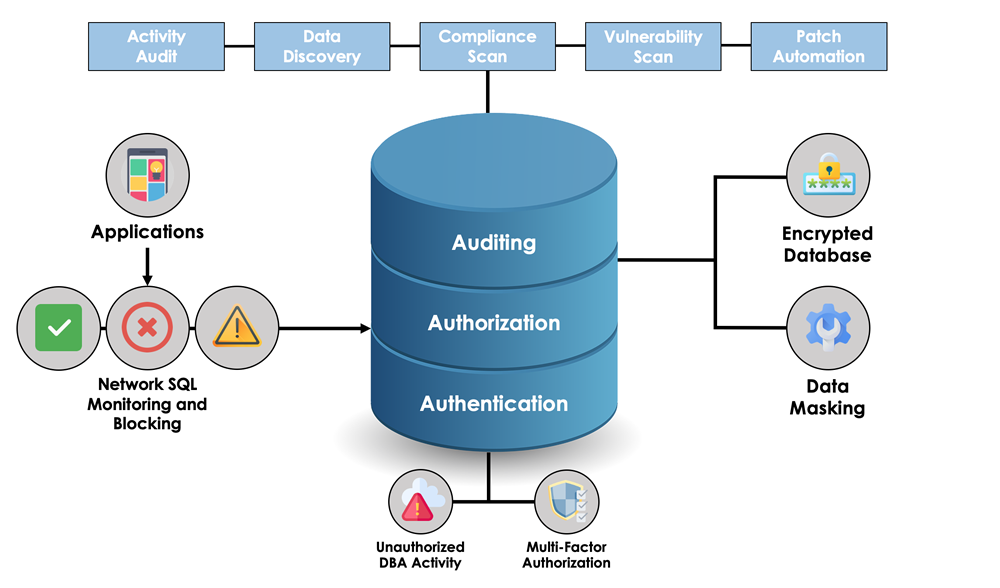
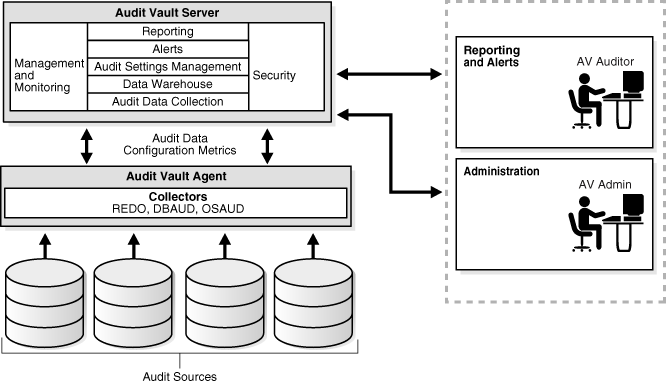
- Database Auditing: Nmap scripts can be employed to gather information about the database’s configuration, user accounts, and permissions. This data is essential for assessing the database’s security posture and identifying potential security risks.
Crafting Effective Nmap Oracle Scripts
Nmap’s scripting language, Lua, provides a flexible and powerful environment for creating custom scripts. These scripts typically leverage the Nmap API to interact with the target system and gather information. Some key components of an effective Nmap Oracle script include:
- Target Selection: The script should specify the target system or range of systems to be scanned. This can be accomplished using IP addresses, hostnames, or network ranges.
- Protocol and Port Identification: The script should define the specific protocol and port used by the Oracle database service. This information is essential for establishing a connection with the database.
- Authentication Credentials: If the database requires authentication, the script should provide the necessary credentials. This can include username, password, and other authentication parameters.
- Script Logic: The heart of the script involves the specific actions to be performed against the database. This could include querying for specific information, testing for vulnerabilities, or verifying configuration settings.
- Output Formatting: The script should define how the collected information is presented to the user. This could include formatted text, XML output, or integration with other reporting tools.
Benefits of Employing Nmap Oracle Scripts
Utilizing Nmap Oracle scripts offers several advantages for database security professionals and administrators:
- Enhanced Security Posture Assessment: Nmap scripts provide a comprehensive view of the database’s security posture, identifying potential vulnerabilities and misconfigurations that could be exploited by attackers.
- Early Detection of Vulnerabilities: By regularly scanning for vulnerabilities using Nmap scripts, security professionals can identify and address potential threats before they are exploited by malicious actors.
- Automated Vulnerability Scanning: Nmap scripts automate the process of vulnerability scanning, saving time and effort for security teams. This allows for more frequent scans and faster identification of security issues.
- Improved Database Auditing: Nmap scripts can be used to gather detailed information about the database’s configuration, user accounts, and permissions, providing a comprehensive audit trail.
- Cost-Effective Security Solution: Nmap is an open-source tool, making its scripting capabilities readily available without any licensing costs.
Practical Applications of Nmap Oracle Scripts
Nmap Oracle scripts find practical applications in various security scenarios, including:
- Penetration Testing: Security professionals use Nmap Oracle scripts to identify vulnerabilities in target databases during penetration testing exercises. This helps to assess the overall security posture of the database system and identify potential attack vectors.
- Vulnerability Management: Nmap scripts can be integrated into vulnerability management systems to automate the process of scanning for vulnerabilities in Oracle databases. This ensures that security teams are aware of any potential threats and can take appropriate remediation actions.
- Security Auditing: Nmap scripts can be used to perform regular security audits of Oracle databases, ensuring that the database is properly configured and protected against potential attacks.
- Database Hardening: Nmap scripts can be used to identify potential misconfigurations in the database and recommend best practices for hardening the database against attacks.
FAQs on Nmap Oracle Scripts
Q: What are the prerequisites for using Nmap Oracle scripts?
A: To effectively use Nmap Oracle scripts, users should have a basic understanding of Nmap’s scripting language (Lua) and possess knowledge of Oracle database concepts, including its services, ports, and authentication mechanisms.
Q: Are Nmap Oracle scripts compatible with all versions of Oracle?
A: While Nmap scripts can be adapted to work with various Oracle versions, compatibility may vary depending on the specific script and the Oracle database version. It is essential to verify compatibility before using any script.
Q: How can I create my own Nmap Oracle scripts?
A: Nmap’s Lua scripting language provides a comprehensive framework for creating custom scripts. Users can leverage the Nmap API to interact with the target system and perform specific actions against the Oracle database. Numerous online resources, including the Nmap documentation and community forums, provide guidance on script development.
Q: Are there any security concerns associated with using Nmap Oracle scripts?
A: As with any network scanning tool, it is crucial to use Nmap Oracle scripts responsibly and ethically. Ensure that you have the necessary permissions before scanning any target system and avoid scanning systems without explicit consent.
Tips for Effective Nmap Oracle Script Utilization
- Thorough Script Testing: Always test your Nmap Oracle scripts thoroughly before deploying them in a production environment. This helps to ensure that the script functions as expected and does not cause any unintended consequences.
- Regular Script Updates: Keep your Nmap Oracle scripts updated with the latest vulnerabilities and security patches. This ensures that your scans are comprehensive and effective.
- Integration with Other Tools: Nmap scripts can be integrated with other security tools, such as vulnerability management systems and intrusion detection systems, for a more comprehensive security solution.
- Documentation and Best Practices: Maintain thorough documentation of your Nmap Oracle scripts, including their purpose, functionality, and any known limitations. This helps to ensure that others can understand and utilize the scripts effectively.
Conclusion
Nmap Oracle scripts offer a potent toolset for security professionals and administrators seeking to assess and enhance the security posture of Oracle databases. By leveraging Nmap’s scripting capabilities, users can automate vulnerability scanning, perform comprehensive audits, and identify potential threats before they are exploited. With proper understanding and responsible utilization, Nmap Oracle scripts can significantly contribute to a robust and secure database environment.




Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of Nmap for Oracle Database Security Audits. We hope you find this article informative and beneficial. See you in our next article!