Unveiling the Secrets of Windows Domain Controllers: A Comprehensive Guide to Nmap Reconnaissance
Related Articles: Unveiling the Secrets of Windows Domain Controllers: A Comprehensive Guide to Nmap Reconnaissance
Introduction
With great pleasure, we will explore the intriguing topic related to Unveiling the Secrets of Windows Domain Controllers: A Comprehensive Guide to Nmap Reconnaissance. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Secrets of Windows Domain Controllers: A Comprehensive Guide to Nmap Reconnaissance
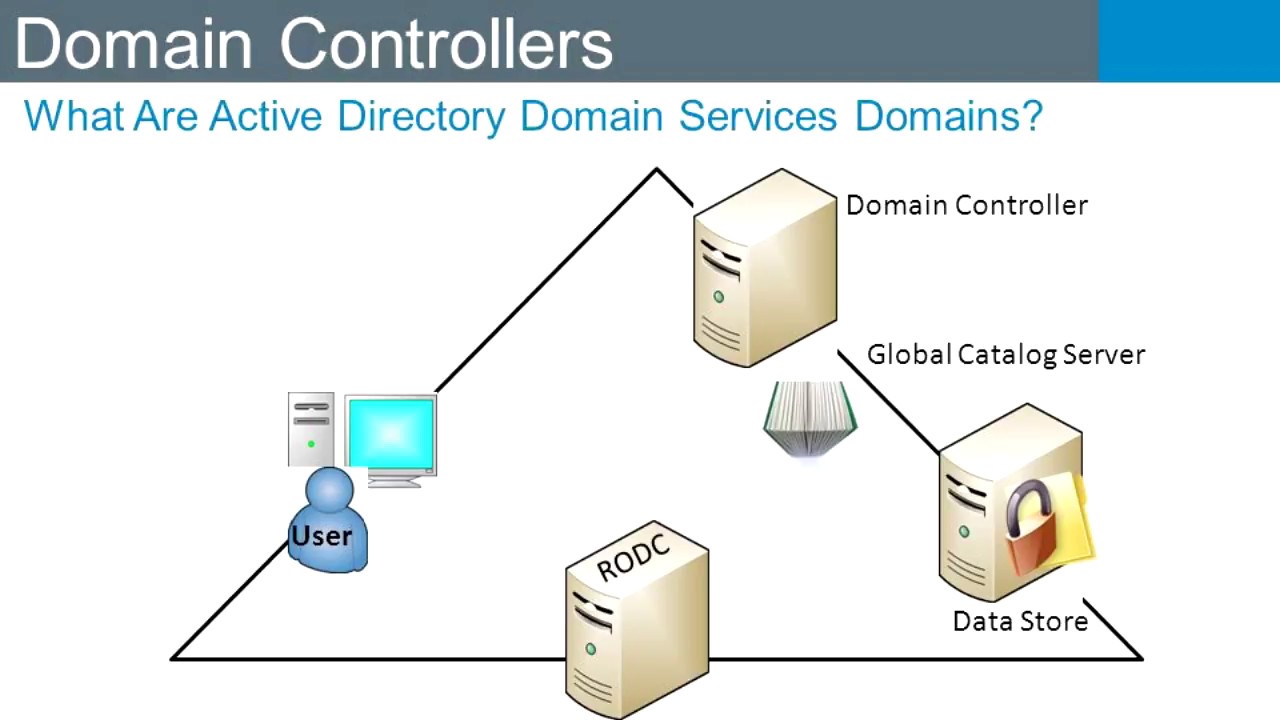
In the realm of network security, understanding the intricate workings of a Windows domain controller (DC) is paramount. These critical servers act as the central authority within a Windows Active Directory (AD) environment, managing user accounts, group policies, and security settings for all connected computers. For security professionals, gaining visibility into the configuration and vulnerabilities of these servers is crucial. This is where Nmap, a powerful network scanning tool, plays a vital role.
Nmap: A Network Security Analyst’s Toolkit
Nmap, short for Network Mapper, is a versatile and widely-used open-source network scanner. It empowers security professionals to discover hosts, identify running services, detect open ports, and gather valuable information about network infrastructure. When applied to Windows domain controllers, Nmap becomes an indispensable tool for:
- Discovering Domain Controllers: Nmap can quickly identify all domain controllers within a network by scanning for specific services and protocols associated with AD, such as Kerberos (TCP/UDP port 88), LDAP (TCP/UDP port 389), and DNS (TCP/UDP port 53).
- Identifying Open Ports and Services: By scanning the target domain controller’s ports, Nmap reveals the services running on the server. This information is crucial for understanding the server’s functionality and potential attack vectors.
- Detecting Vulnerabilities: Nmap can identify known vulnerabilities in the operating system, applications, and services running on the domain controller. This information allows security professionals to prioritize patching efforts and mitigate potential risks.
- Understanding Network Topology: Nmap can map the network infrastructure by identifying interconnected devices and their roles. This provides a comprehensive view of the network’s structure, helping security professionals identify potential attack paths.
Nmap in Action: A Practical Example
Imagine a scenario where a security professional needs to assess the security posture of a company’s Windows domain controller. Using Nmap, the professional can perform a comprehensive scan, gathering vital information:
-
Initial Scan: A basic Nmap scan with the
-sTflag (TCP SYN scan) can identify all active hosts on the network, including the domain controller. -
Port Scan: A port scan targeting the domain controller’s IP address with the
-p-flag (all ports) will reveal the open ports and services running on the server. -
Version Detection: Using the
-sVflag, Nmap can identify the versions of the operating system and services running on the domain controller. This information can help pinpoint potential vulnerabilities based on known exploits. - Vulnerability Scanning: Nmap can integrate with vulnerability databases like NVD (National Vulnerability Database) to identify known vulnerabilities present on the domain controller.
- Script Scanning: Nmap’s scripting engine allows for more advanced scanning capabilities, such as detecting specific vulnerabilities, identifying misconfigurations, and gathering additional information about the target server.
Beyond Basic Scanning: Advanced Techniques
Nmap offers a range of advanced techniques for gaining deeper insights into domain controllers:
- OS Fingerprinting: Nmap can identify the operating system running on the domain controller by analyzing its response patterns. This information can help determine the specific security patches and updates installed on the server.
- Service Detection: Nmap can identify the specific services running on the domain controller, such as Active Directory Domain Services, DNS server, and Kerberos authentication server. This information allows security professionals to tailor their security assessments based on the server’s role within the network.
- Network Mapping: Nmap can map the network topology, identifying devices connected to the domain controller and their relationships. This information is crucial for understanding potential attack paths and identifying critical assets within the network.
- Exploitation: While Nmap is primarily a reconnaissance tool, it can be used to exploit known vulnerabilities in the domain controller. However, this practice should be undertaken with extreme caution and only in controlled environments.
FAQs: Addressing Common Questions
Q: What are the essential ports to scan on a domain controller?
A: The essential ports to scan on a domain controller include:
- TCP/UDP 88: Kerberos authentication server
- TCP/UDP 389: LDAP (Lightweight Directory Access Protocol)
- TCP/UDP 53: DNS (Domain Name System)
- TCP/UDP 445: SMB (Server Message Block)
- TCP 135: RPC (Remote Procedure Call)
- TCP 443: HTTPS (Hypertext Transfer Protocol Secure)
Q: How can Nmap help identify potential vulnerabilities on a domain controller?
A: Nmap can identify potential vulnerabilities by:
- Version Detection: Identifying the versions of the operating system and services running on the domain controller, which can reveal known vulnerabilities based on exploits.
- Vulnerability Scanning: Integrating with vulnerability databases like NVD to identify known vulnerabilities present on the domain controller.
- Script Scanning: Utilizing Nmap’s scripting engine to detect specific vulnerabilities and misconfigurations.
Q: Is it ethical to scan a domain controller with Nmap without authorization?
A: Scanning a domain controller without authorization is generally considered unethical and may be illegal depending on the jurisdiction. It is essential to obtain explicit permission from the network owner before performing any security scans.
Q: What are some best practices for using Nmap to scan domain controllers?
A: Best practices for using Nmap to scan domain controllers include:
- Obtain authorization: Always obtain explicit permission from the network owner before performing any scans.
- Start with a basic scan: Begin with a basic scan to identify active hosts and open ports.
- Use specific scan types: Choose scan types that minimize network impact, such as SYN scans.
- Limit the scan scope: Target only specific IP addresses or subnets relevant to your investigation.
- Use Nmap’s scripting engine: Leverage Nmap’s scripting engine for advanced scanning and vulnerability detection.
- Document your findings: Maintain detailed records of your scan results for future analysis and reporting.
Tips for Effective Domain Controller Scanning
- Prioritize critical services: Focus your scanning efforts on ports and services known to be essential for domain controller functionality.
- Utilize Nmap’s scripting engine: Explore Nmap’s scripting engine to identify specific vulnerabilities and misconfigurations related to domain controllers.
- Integrate with other security tools: Combine Nmap with other security tools, such as vulnerability scanners and penetration testing frameworks, for a comprehensive assessment.
- Stay up-to-date with security updates: Regularly update Nmap and your vulnerability databases to ensure you are using the latest features and information.
- Practice ethical hacking: Conduct your scans ethically and responsibly, always obtaining authorization and minimizing network impact.
Conclusion
Nmap, when used responsibly and ethically, is a powerful tool for gaining valuable insights into the security posture of Windows domain controllers. By leveraging its capabilities for discovery, port scanning, vulnerability detection, and network mapping, security professionals can identify potential weaknesses, prioritize remediation efforts, and enhance the overall security of their Active Directory environments. Remember, the key to effective domain controller security lies in proactive reconnaissance, continuous monitoring, and a commitment to maintaining a secure and resilient network infrastructure.
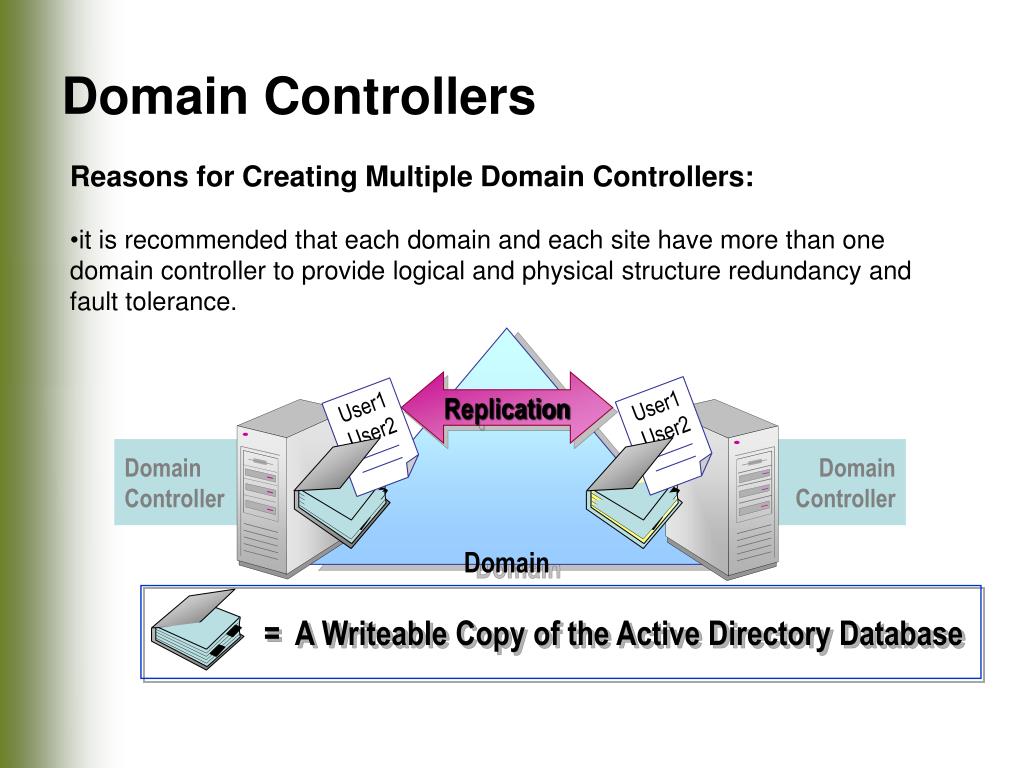
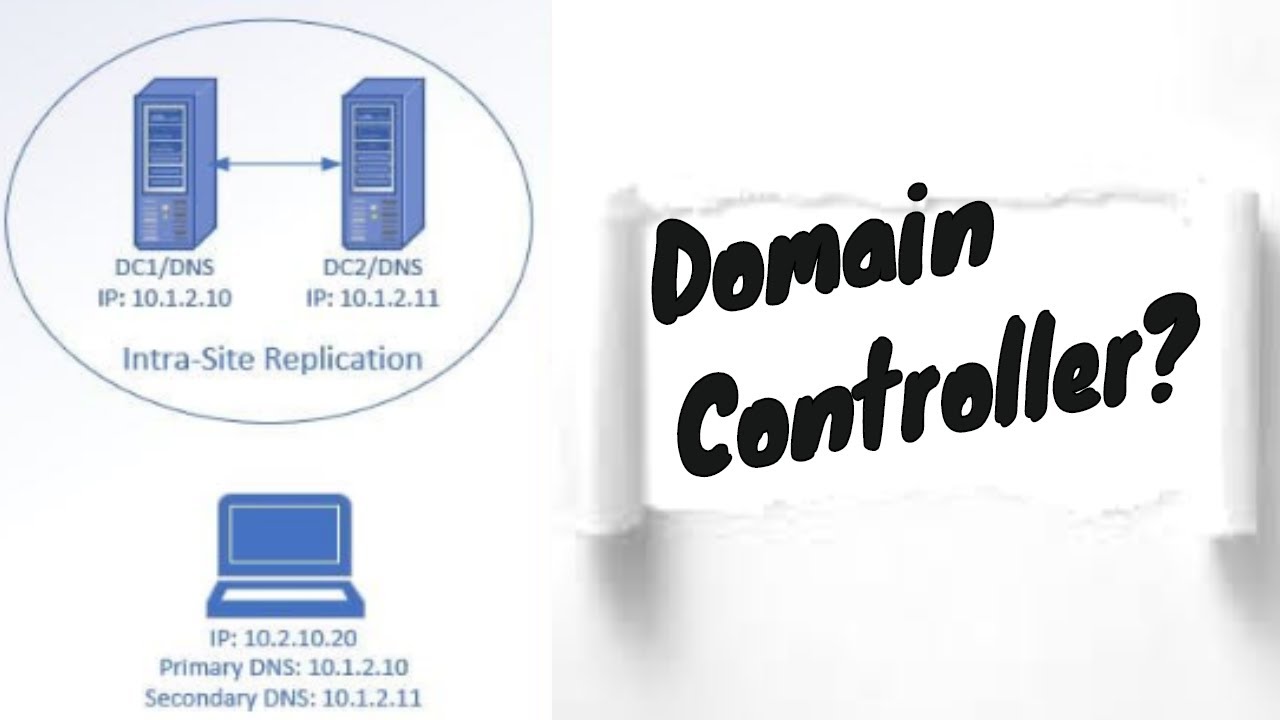



Closure
Thus, we hope this article has provided valuable insights into Unveiling the Secrets of Windows Domain Controllers: A Comprehensive Guide to Nmap Reconnaissance. We appreciate your attention to our article. See you in our next article!